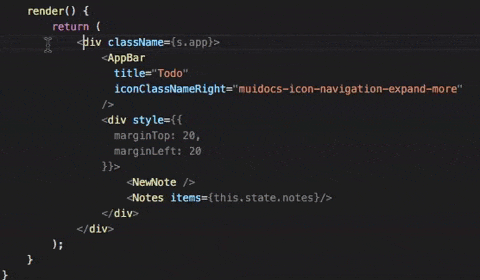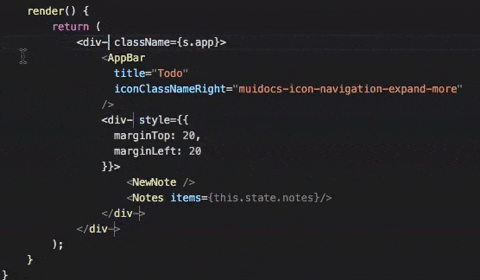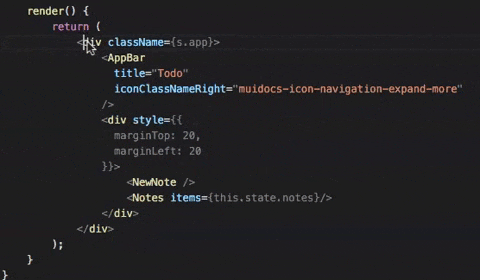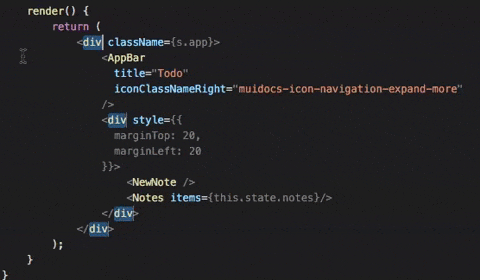
React is undoubtedly one of the most popular JS libraries to build applications. It is also one of the most actively developed libraries which means instant bug fixes and security patches. React has many advantages, but may fall susceptible to security threats. Here are a few recommendations that we share based on our vast experience of working with this technology.
(Know more about our proficiency in Front-end Technologies)
Cross-site scripts and URL injections are some of the most common and serious attacks that affect applications in general. These vulnerabilities are targeted to steal sensitive user data and capture user input to steal credentials and card information.
We have made a list of some best practices that will help you enhance the security of React applications. Do have a look!
Protection against XSS
Your application may have some vulnerabilities that hackers can exploit and insert data in your code that your app treats as part of the code. This in turn gives the attacker the access to make requests to the server and even captures user inputs to steal sensitive credentials.
The injection might look like this:
Code!<script>alert(“malicious code”)</script>
Here’s what the same thing looks like with some protection against XSS:
Code!<script>alert(“malicious code”)</script>
< and < being interpreted as < and >, the browser won’t confuse the data for code.
You can also use:
- Using the createElement() API.
- Using JSX auto escape feature.
- Using dangerouslySetInnerHTML to set HTML directly from React instead of using the error-prone innerHTML.
Adding End-to-End Encryption
Almost every real-time communication application that you’re using comes with End-to-End encryption as standard.
End-to-end encryption means that nobody else other than the parties involved can read the messages. It’s made possible by encryption technology that ensures that the message is encrypted just as it leaves the sender and can only be read once it reaches the intended receiver.
To get E2E in your React application you have to rely on a vendor that provides the tools and kits to ensure secure encryption. Virgil for example is a vendor that provides a platform and JavaScript SDK to create, store, and offer robust E2E secure encryption via public/private key technology.
HTTP Authentication
There are several ways to make authentication secure in your application. Pay special attention to the client-side authentication and authorization because typically they’re ones subject to security flaws.
You can use one of these to ensure your application safety
JSON Web Token (JWT)
- Move your tokens from localstorage to an HTTP cookie since it’s fairly easy to extract from local storage.
- Keep, sign, and verify the secret keys in the backend
- Avoid decoding the token on the client-side and ensure that the payload is small.
- HTTPS over HTTP under any circumstances
Other methods:
- OAuth
- AuthO
- React Router
- PassportJs
Rendering HTML
You should always sanitize dynamic values that you assign to dangerouslySetInnerHTML. The recommended sanitizer to use is DOMPurify.
Import purify from “dompurify”;
<div dangerouslySetInnerHTML={{ __html:purify.sanitize(data) }} />
DDoS prevention
Denial of service happens when the app is not secure or it’s unsuccessful in masking the IPs of services. As a result, some services stop because they can’t interact with the server.
One way to deal with these issues is to just limit the number of requests to a given IP from a specific source.
Or you can always-
- Add app-level restrictions to the API.
- Make calls on the server and NOT on the client-side.
- Add some tests to secure the app layer.
Keep Your Dependencies Updated
There are a lot of third-party dependencies that you use that are patched regularly for security reasons. They can prove to be risky if not updated.
Update your dependencies regularly via security patches and ensure that you leave no backdoor vulnerable for attacks. Try using npm-check-updates to discover dependencies that are out of date. And update if needed to ensure that you’re covered.
Keep An Eye On Library Code
Third-party libraries. Useful? Yes. Risky? A little.
These libraries, modules, or APIs in most cases will help you fast track your development but sometimes they might take your application down with their flaws.
That shouldn’t stop you from using some great third-party offerings. Just a word of caution though, ensure that you are aware of the vulnerabilities, their scale, and workarounds.
And lastly, keep them updated and patch the old ones, just to make your application airtight.
We hope that you find these practices useful and employ some or all to keep your React applications secure and in shape. Do let us know if you’re struggling with some enterprise-wide dependable implementation, we are here to lend a hand. Get in touch with us here.