The timing of this Apple’s urgent security update is sure to raise some questions as it’s happening in the same time frame as the Pegasus hacks. According to the reports, the spyware tool turned mobile phones of journalists, activists, and others into portable surveillance devices, granting complete access to sensitive information stored in them.
The most recent 0-day bug patch that was released this Monday was in the line of 13 releases that Apple has made since the start of this year. Apple has fixed these vulnerabilities for all of their offerings including iOS, iPadOS, and macOS for which Apple claims that the flaw was actively being exploited, until after Apple released the patch.
The update fixes a memory corruption issue (CVE-2021-30807) in the IOMobileframeBuffer component, which is a kernel extension for managing the screen framebuffer. In essence, the flaw could be abused to execute arbitrary code with kernel privileges.
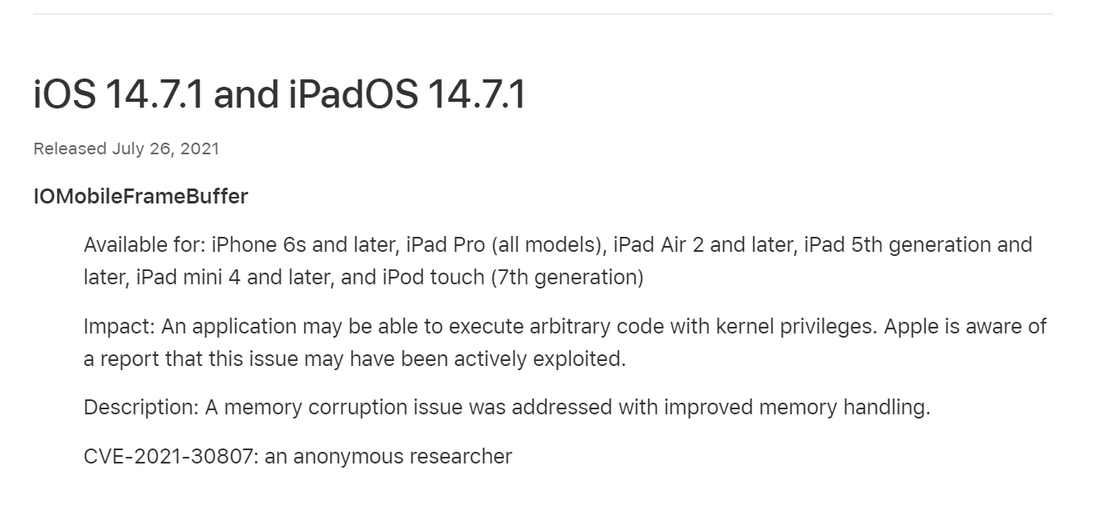
Apple claims that in addition to addressing the issue, they have also improved memory handling. Further details about the exploit have not been disclosed to prevent ill-usage of the information for more severe attacks. An anonymous researcher has been credited by Apple for discovering and reporting the vulnerability.
Here are the other 0-day vulnerabilities that Apple has patched in this year alone including CVE-2021-30807 update —
- CVE-2021-1782 (Kernel) – A malicious application may be able to elevate privileges
- CVE-2021-1870 (WebKit) – A remote attacker may be able to cause arbitrary code execution
- CVE-2021-1871 (WebKit) – A remote attacker may be able to cause arbitrary code execution
- CVE-2021-1879 (WebKit) – Processing maliciously crafted web content may lead to universal cross-site scripting
- CVE-2021-30657 (System Preferences) – A malicious application may bypass Gatekeeper checks
- CVE-2021-30661 (WebKit Storage) – Processing maliciously crafted web content may lead to arbitrary code execution
- CVE-2021-30663 (WebKit) – Processing maliciously crafted web content may lead to arbitrary code execution
- CVE-2021-30665 (WebKit) – Processing maliciously crafted web content may lead to arbitrary code execution
- CVE-2021-30666 (WebKit) – Processing maliciously crafted web content may lead to arbitrary code execution
- CVE-2021-30713 (TCC framework) – A malicious application may be able to bypass Privacy preferences
- CVE-2021-30761 (WebKit) – Processing maliciously crafted web content may lead to arbitrary code execution
- CVE-2021-30762 (WebKit) – Processing maliciously crafted web content may lead to arbitrary code execution
Like any security vulnerability this one is not to be taken lightly considering the threats Apple devices have been exposed to lately. We highly recommend that you move quickly to update your devices to the latest version to avoid exposing your device to attacks associated with the flaw.
About Galaxy
We specialize in delivering end-to-end software design & development services. Our mobile team and UI/UX designers are creative problem-solvers with a decade of experience in all facets of digital and interactive design. We create compelling and human-focused experiences delivered through clean, and minimalist UI. Click here for a free consultation!
